Category: Cybersecurity
-

How a French Woman Lost $850,000 in a Brad Pitt Romance Scam: The Dark Side of Digital Deception
A 53-year-old French woman lost $850,000 after falling victim to an elaborate romance scam involving someone posing as Brad Pitt. Through AI-generated images, emotional manipulation, and convincing narratives, the scammers exploited her trust and emotions, leading to devastating financial and emotional consequences. Her story serves as a powerful warning about the dangers of online deception…
-

8 Game-Changing Trends Shaping Network Security in 2025: AI, SASE, and the Secure Browser Revolution @PaloAltoNtwks
Explore the eight transformative trends reshaping network security in 2025. From secure browsers and AI-driven solutions to the adoption of SASE and post-quantum cryptography, discover how businesses can prepare for the evolving digital landscape and defend against sophisticated cyberthreats.
-

Going Dark: A Deep Dive into Cybersecurity, Conspiracy, and the Shadows of History – A Review of George K. Mehok’s Thriller @gmehok #TBRChallenge #bookchatter #BookReview
Going Dark: A Liberty Unit Novel by George K. Mehok is a cerebral journey into the post-9/11 world of espionage, cybersecurity, and the ongoing battle between freedom and surveillance. Through the eyes of Paul Knox, a conflicted NSA cybersecurity expert, the novel explores the complexities of modern warfare, digital security, and the unseen forces shaping…
-

The Future of AI: Major Trends and Predictions for the Next 5 Years
Discover how artificial intelligence will shape the next five years with breakthroughs in automation, cybersecurity, and cloud strategies. Learn how businesses can leverage AI-driven solutions to stay competitive, secure, and efficient in a rapidly evolving digital landscape.
-

2024 OpenText Cybersecurity Report Reveals Increasing Collaboration Between Nation-States and Cybercrime Rings @OpenText
The 2024 Threat Hunter Perspective by OpenText Cybersecurity highlights the growing collaboration between nation-states and organized cybercrime rings. This report warns of large-scale, highly coordinated cyberattacks targeting global supply chains, critical events, and geopolitical objectives. With nation-states like Russia and China partnering with cybercrime gangs, enterprises face unprecedented risks. The need for robust defense strategies…
-
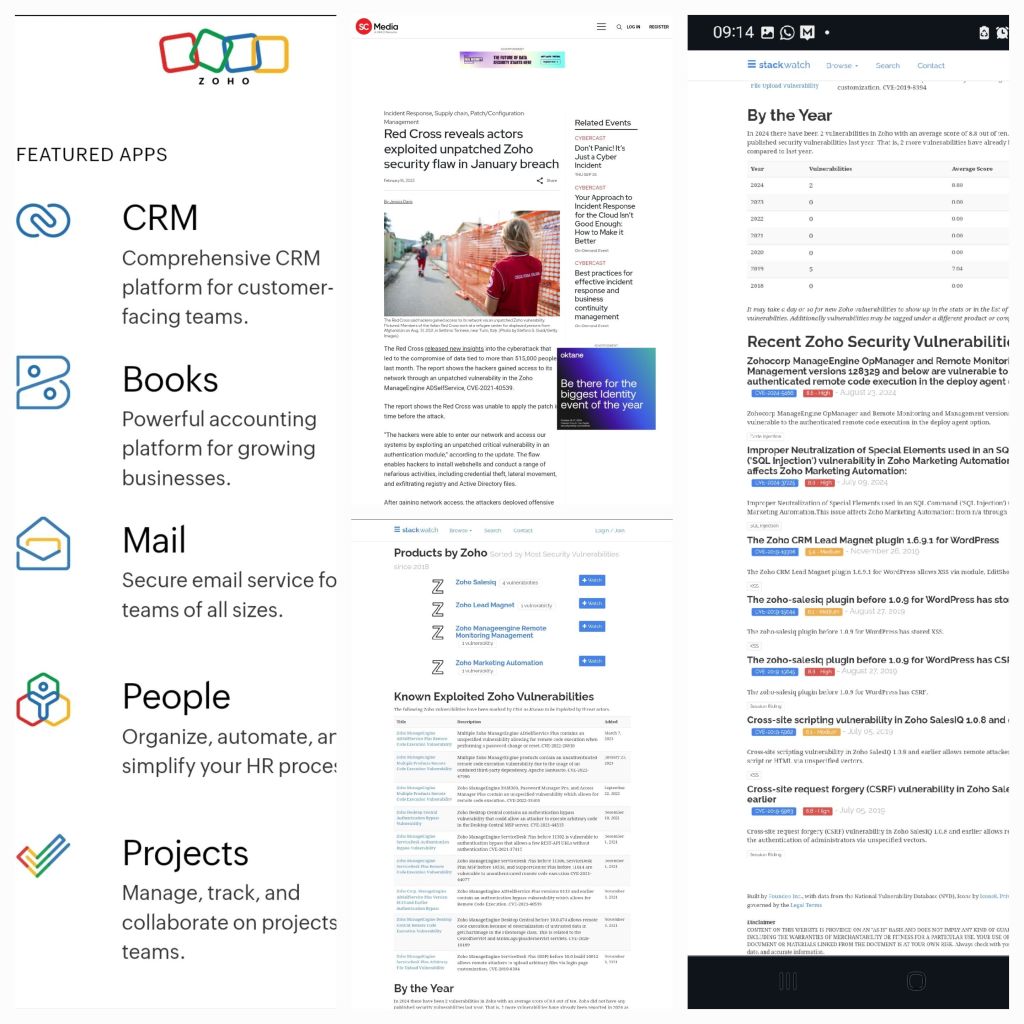
Zoho Product Vulnerabilities: Exploring Legacy Issues and New Security Threats in 2023-2024 @zoho #ZohoOne #ManageEngine #ZohoCRM #ZohoBooks
Discover the critical security vulnerabilities in Zoho products from legacy issues like authentication bypass and SQL injection to the newly uncovered threats in 2023-2024. Learn how zero-day vulnerabilities, API misconfigurations, phishing vulnerabilities, and more pose risks to businesses and what steps Zoho is taking to improve security.
-

Palo Alto Networks Acquires IBM’s QRadar SaaS Assets: Revolutionizing Cybersecurity with AI-Powered Security Solutions #technology #news
Palo Alto Networks has completed its acquisition of IBM’s QRadar SaaS assets, advancing the future of cybersecurity. This move integrates AI-powered threat prevention and next-gen SOC innovations, revolutionizing security operations with the powerful Cortex XSIAM platform.
-

Orrick Settles Data Breach Lawsuits for $8 Million: Key Details and Implications
Dive into the details of Orrick’s landmark $8 million settlement to resolve a class action lawsuit stemming from a significant data breach. Explore the key benefits for affected individuals, the rationale behind the decision to settle, and the implications for cybersecurity practices in today’s digital landscape.
-

Palo Alto Networks Redefines Cloud Security with Cortex XSIAM for Cloud: Empowering SecOps in the Cloud Era @PaloAltoNtwks
Discover how Palo Alto Networks’ Cortex XSIAM for Cloud revolutionizes cloud security operations, empowering SecOps teams with advanced capabilities for real-time threat detection and response in the cloud era.
-

FIDO Technology: The Future of Secure Online Authentication
In a world where digital security is paramount, traditional authentication methods are falling short. Dive into the world of FIDO technology, a game-changer that promises to redefine online security. From biometrics to hardware tokens, discover how FIDO is making online authentication more secure and user-friendly. Explore its core principles, the role of biometrics and hardware…